Why Risk Over Time Matters More Than a Single Test
As part of my time spent as a penetration tester, I have written and reviewed hundreds of reports on the security posture of countless clients. When reviewing these reports, whether from the tester or client perspective, the first thing anyone typically notices is the overall risk or threats currently facing the organization.
However, I would argue that one of the most important metrics I look at for returning clients is their security posture over time. If you are senior management, this is the metric that should interest you the most. In the following article, I will outline why this matters and how to ensure your organization is moving in a positive direction.
What Consistent Testing Really Tells You
In my professional experience, it is incredibly rare to test a client whose network security is without issues, or even limited to only a few low-risk findings. The few cases where I have seen this are clients that consistently engage in annual penetration tests and actively use the results to strengthen their security posture.
When you have recurring tests, I believe it becomes less important to focus solely on your current security posture and more important to evaluate your posture over several years. This historical view helps determine whether your organization is genuinely improving and withstanding new and evolving attack methods.
The Role of Management in Turning Findings Into Action
An effective penetration test report should provide clear and actionable remediation or mitigation guidance for every reported security finding. With this information in hand, management’s responsibility is to create a plan of action to remediate these issues in a timely and effective manner.
That said, a good penetration tester understands that some security recommendations may conflict with business needs. In these cases, it is management’s responsibility to determine whether a risk should be accepted.
When Mitigation Isn’t Possible: Detection and Response Still Matter
Responsibility then returns to the penetration tester to provide mitigations that minimize business impact. If even mitigation negatively impacts business functionality, the tester should, at a minimum, assist with recommendations for implementing effective detection and response procedures for those accepted risks.
Without digressing too much, this also highlights the value of engaging in Purple Team exercises with your penetration testing partner, when available.
Using Historical Trends to Measure Security Program Maturity
Tracking historical risk trends can be a strong indicator of a security team’s conscientiousness. Barring new or novel exploit techniques, or business-critical functionality that prevents certain mitigations, your organization should see a positive year-over-year trend in penetration test results.
A lack of this positive trend may indicate that security findings are not being addressed effectively, or that sufficient planning and accountability are missing within the security program.
Real-World Example
To provide a real-world example, I worked with a client we tested over multiple years. One vulnerability identified during an engagement involved several Active Directory Certificate Services (AD CS) templates vulnerable to the ESC1 exploit.
Without going too deep into technical detail, the core issue with this vulnerability is that a certificate requester leveraging a vulnerable template can specify an arbitrary Subject Alternative Name (SAN). This means that any user, regardless of permissions, can request a certificate for an administrator account, allowing for a straightforward privilege escalation [2].
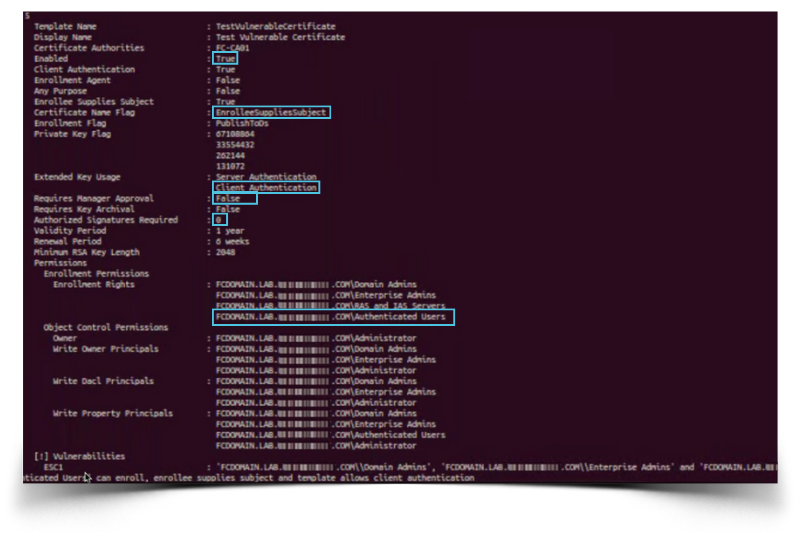
The above image is an example of the exact circumstances one would expect for an ESC1 vulnerable template [1].
As mentioned earlier, this client had several ESC1-vulnerable templates enabled in their AD CS infrastructure. The findings were reported and detailed remediation and mitigation guidance were provided, along with supporting documentation.
Fast forward to the following year when we tested the same client. While enumerating their AD CS environment, several ESC1-vulnerable templates were discovered. After cross-referencing the prior year’s report, it was determined that these were not the same templates previously identified.
This led to the conclusion that while the client had remediated the original vulnerable templates, they failed to implement internal procedures for securely creating new ones.
What Recurring Vulnerabilities Say About Your Security Program
Recurring vulnerabilities like this are a strong indicator of a low-conscientiousness security program. Fixing individual findings without addressing the underlying process issues almost guarantees the same problems will resurface over time.
Accountability After the Report Is Delivered
As a manager, it is your responsibility to ensure that after a penetration test report is delivered, your security team implements a concrete remediation plan—clearly defining how and when findings will be addressed.
If remediation is not feasible, effective mitigations must be put in place, including tuned alerting and response procedures to detect exploitation attempts early. Proper procedural documentation, ownership, and long-term accountability are critical to preventing the same issues from reappearing year after year.
Citations
[1] https://www.beyondtrust.com/blog/entry/esc1-attacks
[2] https://specterops.io/wp-content/uploads/sites/3/2022/06/Certified_Pre-Owned.pdf